812.67 million malware attacks occurred in the single year of 2018. This number is growing with the rise of technological advances. Approximately 92% of those attacks were delivered through a type of service that about everyone uses: Email. This attack is more commonly known as a phishing, to look like a legit link in an email.
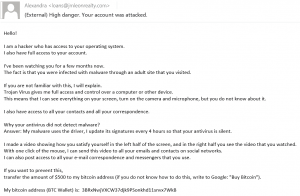
But what about the other 8% you ask? Well, this blog has all the information you need.
Heritage says, “In terms of the threats the U.S. faces, nation-state hackers are the most serious. Russia presents the most sophisticated cyber threat, with China as a close second.” Globally, these two powerhouses have come out to be the origin of 30% of all cyberattacks. Most of the ones that get surfaced on the news because of sophistication are from Russia.
If you are not a technology geek like me, it’s okay! Here are some key terms to help you understand what is happening to get the big picture.
- A network security vulnerability (or sometimes referred to as a cyber threat) is a weakness or flaw which can be exploited by a malicious actor to perform unauthorized actions within a computer system.
- Hacking, which is a term that is always thrown around, is the act of compromising digital devices and networks through unauthorized access to an account or computer system. You must understand that hacking is not always bad. There are many types of hackers which include:
- Black Hat Hackers– the bad guys; what this blog covers.
- White Hat Hackers– the good guys a.k.a. “ethical hackers”
- Grey Hat Hackers– blend of both black hat and white hat; both good and evil.

RECENT MAJOR RUSSIAN CYBERCRIMES
So the question stands: what’s really going on with Russian hacking? To address this question let’s take a look at some of the most recent and most damaging cyber attacks that have been pushed out from Russia.
On December 13, 2020, FireEye announced the discovery of a highly sophisticated cyber intrusion that leveraged a commercial software application made by SolarWinds. The attackers infiltrated the network and inserted a package of malware into the software. This malware payload included a backdoor into the product which is a method by which authorized and unauthorized users are able to get around normal security measures and gain high level user access (aka root access) on a computer system, network or software application. Backdoors are like they sound: a back door into the system like a back door into a house to be unnoticed.
This means that each and every one of SolarWinds customers that downloaded the newly infected software now granted the hackers access to their computer system and network. The worst part was: they didn’t even realize they were clicking on a Trojan virus and granting the access.
Many companies worldwide use SolarWinds’ Orion software to monitor their computer networks. Nearly 18,000 customers were infected, including U.S. government networks and private companies’ systems. The hackers had access to this information from March to June of 2020.
Russia’s foreign intelligence service, the SVR, is believed to have carried out the attack, according to cybersecurity experts who cite the extremely sophisticated nature of the attack.
In 2015, A Russian-based cybercrime group, named Peace, infiltrated the large professional site known as LinkedIn — stealing more than 117 million username and password combinations. The same group in 2016 decided it wanted more, so they targeted the once-beloved MySpace with the same techniques — this time scoring over 360 million accounts. The techniques they used have been carried to today and compromised another 100 million systems.
Another infamous russian-based group called Kremlin Hackers, use a slightly similar technique. They use basic — but often effective techniques — daily to pry open practically any vulnerable network they find across the U.S. and global internet. The latest of their sly crimes breached the Republican National Committee (RNC) last week, although the party denies that any data was stolen.

Lots of cyber-organizations have sent warnings of hundreds of attempted brute-force hacker intrusions around the world, all carried out by Unit 26165 of Russia’s GRU military intelligence agency, also widely known as Fancy Bear or APT28.
But cybersecurity agencies warn that the Fancy Bear campaign has nonetheless successfully breached multiple entities and exfiltrated emails from them—and that it’s not over. “This lengthy brute force campaign to collect and exfiltrate data, access credentials and more, is likely ongoing, on a global scale,” the NSA’s director of cybersecurity Rob Joyce wrote in a statement accompanying the advisory.
Written By: Hope Deckard
November 10, 2021

