Cybersecurity. When you think of that word, what do you think of? Hackers pounding away in a dark corner? That old PBS TV series Cyberchase? Or, you may not even know what it means! Never fear, I am here to make sure you understand the basics of this vast concept.

There are many words most people have heard that cybersecurity gets loosely associated with such as IT security, system security, network (or WIFI or Internet) protection, computer security, and many more! The truth is: all of these hit along the lines of cybersecurity.
To understand this thirteen letter word, let’s break it down into digestible pieces:
Cyber = of, relating to, or involving computers or computer networks (such as the Internet)
Security = the quality or state of being secure: such as
a: freedom from danger : SAFETY
b: freedom from fear or anxiety
c: freedom from the prospect of being laid off (job security)
NOTE: don’t let this fool you, there is no such thing as being 100% secure when it comes to security, alas computer security. Anyone with proper equipment, knowledge, and motive can and will hijack your computer system.
Cybersecurity = measures taken to protect a computer or computer system (as on the Internet) against unauthorized access or attack
There are many security issues and challenges in the world today. One of my all time favorite quotes from Spider-Man that can be applied to the concept of technology is, “With great power, comes great responsibility.” If you think about this with the increase in technological advancements, and how its use is greatly spreading throughout the years, you’ll come to realize that technological advances present new and stronger threats to the world along the way.
What is cybersecurity?
- Cybersecurity is the act of taking precautions to secure an information system with mechanisms such as a VPN, antivirus, and firewall. To understand why we need cybersecurity, let’s take a short dive into the history of cybersecurity.
Brief History of Origins
We have Bob Thomas to thank for the existence of cybersecurity. He was the first to create a worm-like program named Creeper that moved, or hopped, between mainframe computers. This was only an experiment written in 1971 that had no malicious intent or harm done except the words “I’M THE CREEPER; CATCH ME IF YOU CAN” displayed on the current target computer.
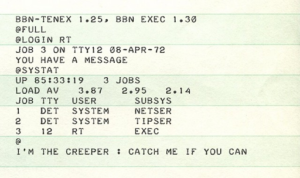
This was later intentionally eliminated by the first self-replicating worm named Reaper, which acted like anti-virus software to remove Creeper.
First malicious intended cybercrime
“At this point in the history of cyber security, computer viruses began to become less of an academic prank, and more of a serious threat. Increasing network connectivity meant that viruses like the Morris worm nearly wiped out the early internet, which began to spur the creation of the first antivirus software.”
In 1988, Robert Morris began developing a program that could spread slowly and secretly across the Internet. When he released the work on November 2nd of the same year, it began propagating rapidly across the internet. “Computer worms, unlike viruses, do not need a software host but can exist and propagate on their own.”
Within 24 hours, it is estimated to have 6,000 computers at a grinding halt at multiple public and private research centers and colleges such as Harvard, NASA, Princeton, and John Hopkins. FBI reports, “The exact damages were difficult to quantify, but estimates started at $100,000 and soared into the millions.”
Types of Computer Threats
- There are many types of categories of malware (malicious software) and cybercrime that are present in today’s world, let’s review some of the major types so we know what we’re protecting ourselves from.
- Virus- In more technical terms, a computer virus is a type of malicious code or program written to alter the way a computer operates and is designed to spread from one computer to another. A virus operates by inserting or attaching itself to a legitimate program or document that supports macros in order to execute its code. In the process, a virus has the potential to cause unexpected or damaging effects, such as harming the system software by corrupting or destroying data.
- Worm- type of malware that spreads copies of itself from computer to computer. A worm can replicate itself without any human interaction, and it does not need to attach itself to a software program in order to cause damage.
- Trojan- malware that disguises itself as something useful so the user will click activate it.
- Spam and Phishing- schemes aimed at tricking you into providing sensitive information to scammers.
- Some of the lesser known Malware types:
- Ransomware- malicious software that keeps files, folders, confidential documents, and/or whole systems hostage until a ransom is paid.
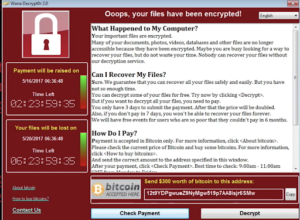
-
- Logic bombs- a kind of virus that waits for a user to execute a certain task, like logging in, or something to happen, like it turning 12:38 PM on Tuesday, to be activated.
- Rootkits– The main purpose of rootkits is to mask malware payloads effectively and preserve their privileged existence on the system.
Now you know that there are vast possibilities of ways to do great damage to an information system. “With great power comes great responsibility.” Not all heroes wear capes…or super suits like Spider-Man. These are the heroes and heroines of protecting you and your computer, and they are all in one crucial area: Cybersecurity.
Written by: Hope Deckard
July 6, 2021

